Do Group Leaders have the ability to ‘delete’ group members from their group? The simple answer is no. Group leaders can make people active and inactive but group leaders do not have the ability to archive or delete group members from a particular group. Some of the vision behind this, is that we never want […]
Read MoreHalloweekend Campus Prep | 255
Each time we have a big invite weekend, there are added stresses to our work days/weeks leading up to the weekend. Sometimes these added stresses cause us to forget or lose track of some of these things we do week in and week out. We get so excited about the weekend to come. We thought […]
Read MoreNew Communication | 254
Have you ever wondered… what are all those options on the New Communication page? Well today, we are going to fill you in! You can find this page here: Rock > People > New Communication Lets first discuss: Communication List In order to use this page, you have to start by selected one of two […]
Read MoreDon’t trust pop-ups | 253
If you’re known to dabble in a little online browsing, odds are you’ve encountered a pop-up once or twice. There are times when a user may think, “Wow, that’s a great deal!” and click on a pop-up. To those users: put down the mouse. Why? That pop-up could be malicious or dangerous. There used to […]
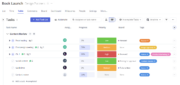
Read MoreTeamwork Tables | 252
Start managing your work more efficiently — Introducing the new Task Table View in Teamwork With the new Task Table View in Teamwork, efficiently managing all of your work is easier than ever before. The new view enables users to add, track, and manage project work much faster. It’s incomparable to other views as you […]
Read MoreTablecloth Sizing | 251
Have you ever wondered what size tablecloth you need? Tablecloth sizing, believe it or not, an actually be kind of confusing! In order to help make your decision easier, I wanted to share with you a Tablecloth calculator! Plug in your size table and select various size tablecloths to see how they will lay across […]
Read MoreDeepfake Videos | 250
Engaging with others through videos has become a standard part of our everyday lives. Whether you’re joining a video conference at work or watching your favorite celebrity on Instagram, videos are everywhere. However, can you really trust what you’re seeing? The rise of deepfake technology could make it difficult to know if what you are […]
Read MoreCheckin FAQs | 249
Here are a couple FAQs to think about if you run into any checkin problems. What if a DreamTeam member can not check in? Are they active in the group within Rock? Is this the time the groups is built to allow checkin? Did they already check into another area during the current timeframe? Growth Track […]
Read MoreKnown Issue Tips | 248
Today we wanted to make you aware of a few new features around known issues that we hope will be helpful. When our team is made aware of a new issue that we believe effects a large portion of our team (Staff or DreamTeam) we will post a notification in a few areas. This notification […]
Read MoreMobile App | Known Issue | 5.26.24
There is currently a known issue where some users are experiencing a delay when opening the CedarCreek Church Mobile App. This experience is not consistent across all devices. We have submitted a support ticket to our developer and will continue to monitor the situation. Updates when available can be found here.
Read More